Bluejacking explained: What it is and how to stay safe

Plenty of people use Bluetooth daily. You might have Bluetooth headphones for your phone or send files via Bluetooth to friends and family. But did you know that same technology can be used against you in a malicious practice called bluejacking? In this guide, we’ll explore what bluejacking is and how to guard against it.
What is bluejacking?
Bluejacking is a type of intrusive behavior that harnesses Bluetooth technology. It involves someone sending unsolicited messages, links, or images to your device via Bluetooth. Those messages can range from simply being annoying to real security threats. Bluejacking doesn’t give the perpetrator access to your personal data or device controls, but it can still be disruptive and potentially dangerous if used for phishing.
How does bluejacking work?
Bluejacking relies on the same Bluetooth technology you’ve probably used to connect headphones or send files between devices. Let’s walk through a typical scenario of a bluejacking attempt. A bluejacker, usually in a crowded place, searches for nearby devices with Bluetooth turned on and set to “discoverable.” These devices send basic information to make pairing easier, like when you open your wireless headphones and your phone immediately pops up a message asking to connect.
A bluejacker, usually in a crowded place, searches for nearby devices with Bluetooth turned on and set to “discoverable.” These devices send basic information to make pairing easier, like when you open your wireless headphones and your phone immediately pops up a message asking to connect.
Bluejacking uses that same system, but instead of trying to connect a device like headphones, the bluejacker sends a Bluetooth message, often in the form of a contact card. These cards don’t require pairing to be received, and your phone may simply show a pop-up asking if you want to accept the contact.
This is similar to how someone might send you a digital business card to share their number. But in a bluejacking attempt, the contact card might have a joke name like “Call Me Maybe 😉” or “Free Wi-Fi Password,” just to get your attention. That’s basically what bluejacking is: a mostly harmless prank.
However, while bluejacking itself doesn’t involve hacking or malware, it can be confusing, and in rare cases, it may trick people into accepting further Bluetooth interactions or links (sometimes, phishing links). That’s when it starts to blur into more serious types of attacks.
Is bluejacking illegal or dangerous?
At first glance, bluejacking may not seem all that dangerous. After all, you have to be very close to someone to send anything to their device via Bluetooth. Plus, even if you can connect, it’s only possible to send simple messages or images, which aren’t necessarily dangerous on their own. However, it’s important to not underestimate bluejacking, as it can, in some cases, pose real risks.
When it comes to the legal side of the matter, legal systems vary around the world, but bluejacking is not technically considered a crime in most places. This is mainly because it doesn't involve anything explicitly illegal, like stealing data or breaking into a device. However, there are cases in which bluejacking attacks could cross legal lines, such as:
- Harassment: If someone repeatedly targets the same person with bluejacking messages, it could be considered harassment.
- Phishing: As touched on earlier, bluejacking messages may contain phishing links that lead to fake websites designed to steal their data.
- Malicious intent: While bluejacking itself doesn’t provide access to data, using it to scare, threaten, or seriously distress someone could have legal consequences.
- Explicit: If someone uses bluejacking to send explicit or illegal content, that may also lead to legal consequences.
Bluejacking vs. other Bluetooth threats
Despite its potential to be used for phishing or harassment, bluejacking is actually one of the least harmful ways intruders can exploit Bluetooth. There are other, notably more dangerous techniques out there, such as bluesnarfing, bluebugging, and bluesmacking.
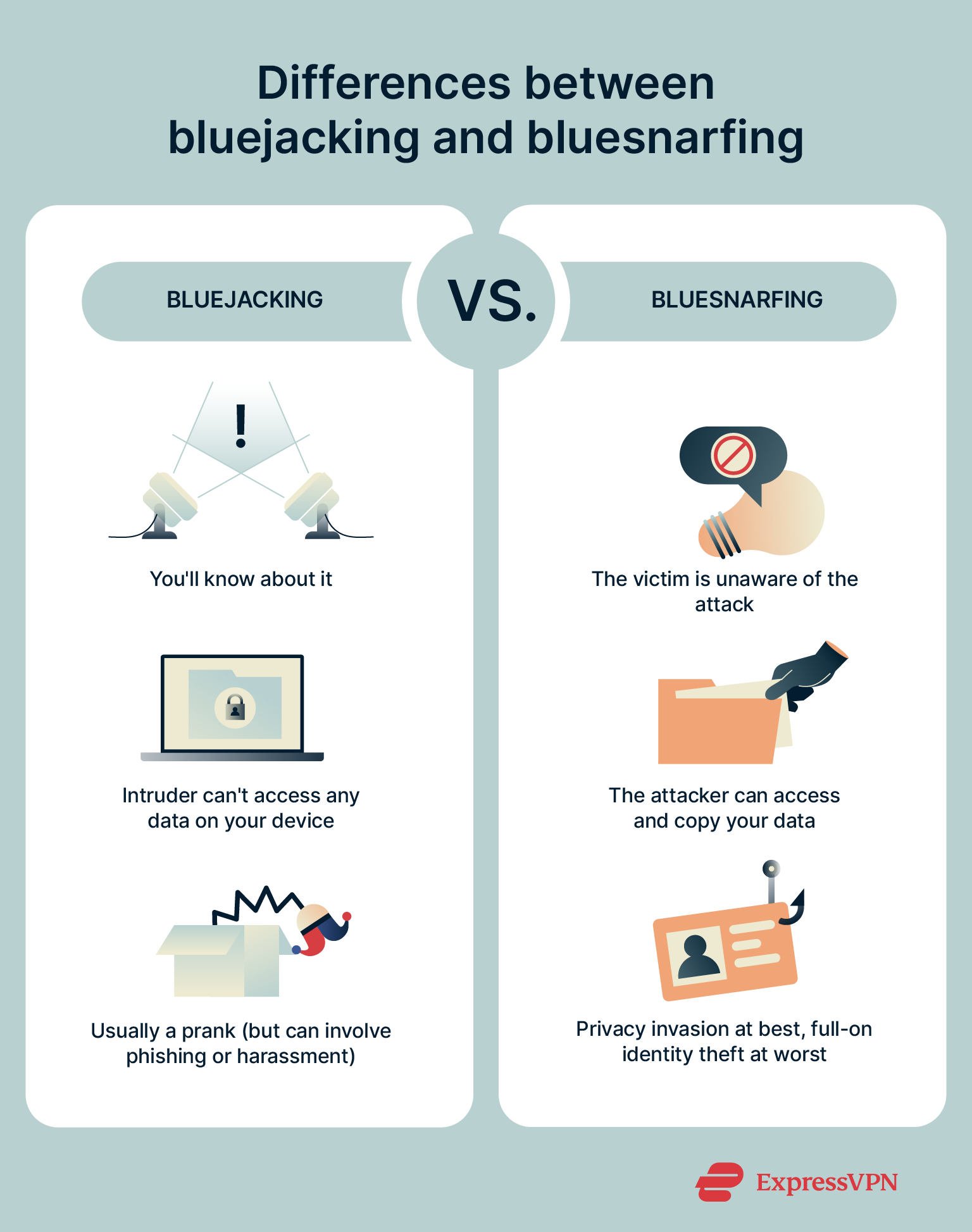
Bluejacking vs. bluesnarfing
Bluesnarfing is a form of cyberattack in which someone uses Bluetooth to secretly connect to your device and access and copy your texts, emails, contacts, and, in some cases, your pictures or private videos. The term comes from “snarfing,” a technical slang for copying data without the owner’s consent.
Here are the key differences between the two:
- Secrecy: With bluejacking, you’ll know something happened: the message pops up on your screen. However, bluesnarfing is much sneakier. The victim usually has no idea that someone else has gained access to their device and data.
- Sophistication: Bluesnarfing attacks are usually much more sophisticated and harder to pull off than bluejacking ones. Hackers often use special tools to exploit bugs in Bluetooth and force a connection, sometimes without the user even knowing or pairing with the device.
- Access: With bluejacking, the attacker never really has access to your device’s contents; they can only send you messages or files. With bluesnarfing, however, they can gain almost unrestricted access to your private content, including your photo gallery, messages, and contacts.
- Severity: While both techniques should be taken seriously, bluesnarfing is clearly more dangerous. Bluejacking might just be a prank or spam, but bluesnarfing can lead to serious privacy breaches, identity theft, or fraud.
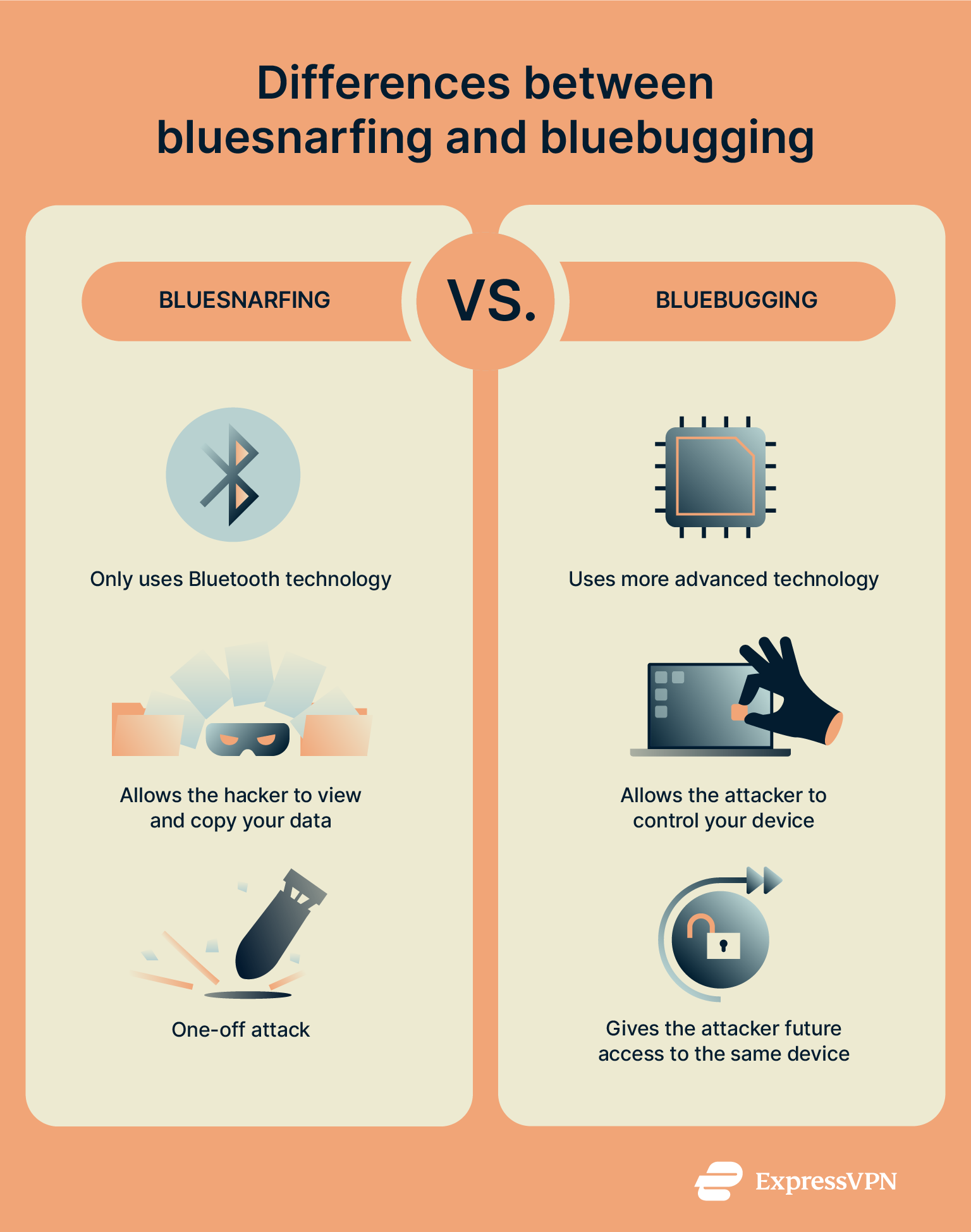
Bluejacking vs. bluebugging
Bluebugging is quite similar to bluesnarfing but arguably even more serious. It involves the attacker using Bluetooth to access a device by exploiting a specific vulnerability in how that device’s Bluetooth is built. While technically possible, attacks like this are extremely rare: Bluetooth vulnerabilities that allow this kind of access are very hard to find and highly valuable.
Once they’re in, they can install a backdoor that lets them reconnect to the device (and access its contents) at a later time. In other words, they “bug” the device, which is where the term bluebugging comes from. With this kind of access, the hacker can access the device’s content, listen in on data transmissions, and even control the device remotely.
Here are some ways this differs from bluejacking:
- Secrecy: Bluebugging is a much more secretive technique than bluejacking. You’ll usually know when you’ve been bluejacked, since a message pops up on your screen. But with bluebugging, victims often don’t realize they’ve been compromised until much later, though this kind of attack is extremely rare, since it requires a high-value vulnerability that’s difficult to find.
- Technology: Bluebugging is much more advanced than bluejacking. It may involve exploiting firmware vulnerabilities or pairing flaws to install backdoor access, and in some cases, it can even involve installing spyware.
- Control: Bluebugging doesn’t just give someone access to your content; it can give them control over the device. Attackers might make remote calls or set up call forwarding so that they receive any calls intended for the device owner.
- Permanence: Bluejacking (and bluesnarfing) is, in most cases, a one-off attack, as the attacker needs to be within Bluetooth range to target each device. But bluebugging can grant ongoing access, even when the attacker is no longer in Bluetooth range.
- Severity: Bluebugging is considered a more serious Bluetooth-based attack. This is because it can seriously invade your privacy and make your device unsafe.
 Again, bluebugging attacks are very rare in real life. They’re much more difficult to carry out than a simple bluejacking prank and require the attacker to discover a Bluetooth vulnerability in the target device. Since finding and reporting this kind of flaw can be very lucrative, anyone who discovers a zero-click vulnerability would likely find it more profitable to sell it rather than exploit it.
Again, bluebugging attacks are very rare in real life. They’re much more difficult to carry out than a simple bluejacking prank and require the attacker to discover a Bluetooth vulnerability in the target device. Since finding and reporting this kind of flaw can be very lucrative, anyone who discovers a zero-click vulnerability would likely find it more profitable to sell it rather than exploit it.
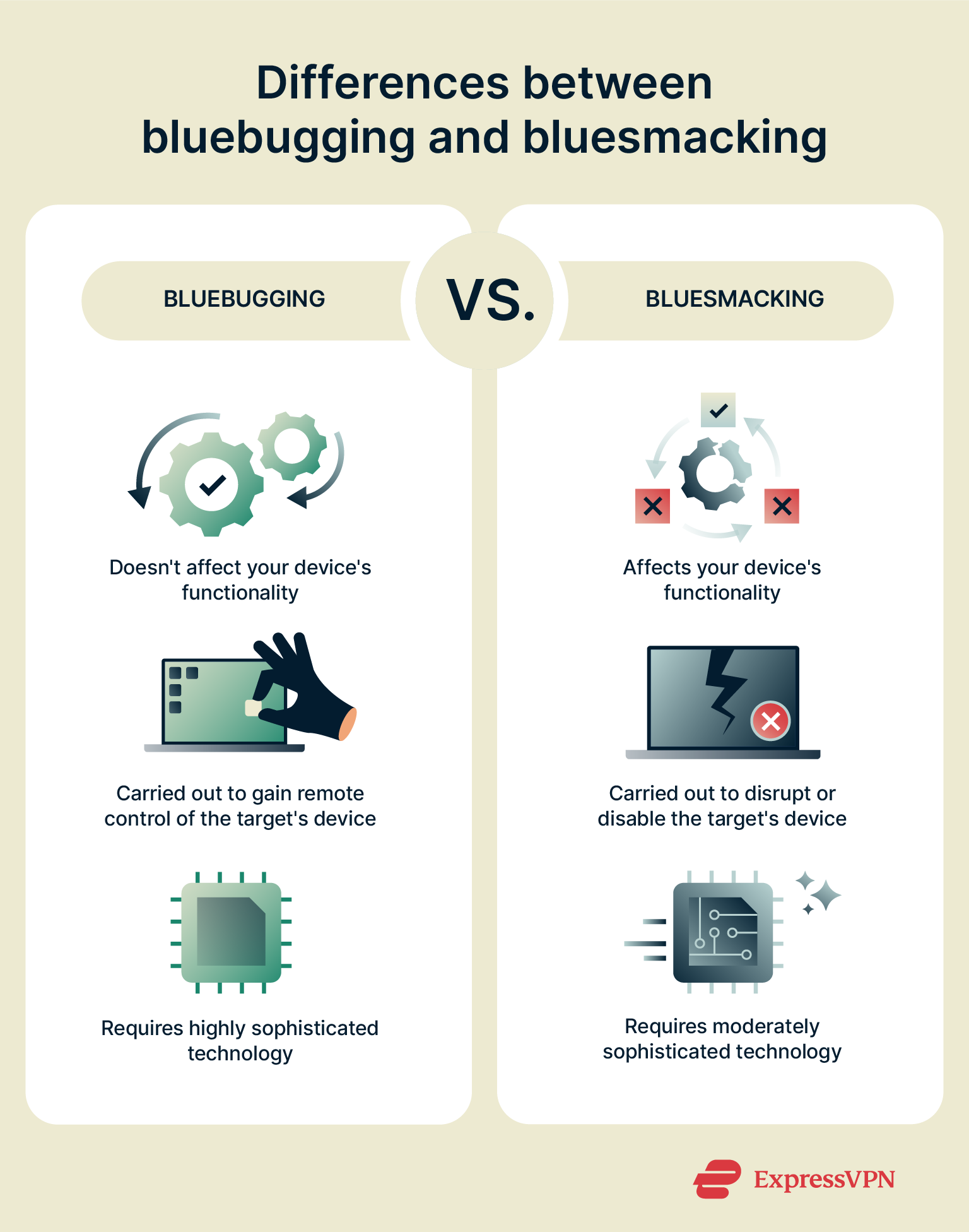
Bluejacking vs. bluesmacking
Yet another Bluetooth-based weapon in the hacker’s arsenal is bluesmacking. This attack is more focused on disrupting a device via Bluetooth rather than stealing data or gaining unauthorized access.
Bluesmacking works through denial-of-service (DoS) attacks carried out over Bluetooth. While DoS attacks are often associated with overwhelming a system using a high volume of data, that’s not always the case. In the context of Bluetooth, an attacker might send a special packet that causes the device’s operating system to crash or reboot, effectively knocking the device offline, even without flooding it.
Here are some of the ways in which this differs from bluejacking:
- Secrecy: Unlike with bluejacking, bluesmacking attacks are initiated in secret.
- Impact: Bluejacking ends with a message or image simply showing up on your screen. Bluesmacking, on the other hand, can knock your device out completely.
- Intent: Bluejacking is often done as a prank. Bluesmacking, on the other hand, is carried out to disrupt or disable the user’s device.
- Sophistication: Bluesmacking is also more advanced than bluejacking.
How to protect yourself from bluejacking
The good news? It’s pretty easy to protect yourself from bluejacking. A few smart Bluetooth habits can go a long way, not just against bluejacking, but also more serious threats like bluebugging and bluesnarfing.
Turn off Bluetooth when not in use
If you tend to leave Bluetooth on all the time, you’re not alone. But keeping it enabled 24/7 also makes your device an easy target.
The simplest defense is to turn Bluetooth off whenever you don’t need it, especially in crowded public places like malls, airports, or train stations. If it’s off, no one can connect to you. Easy.
Make your device non-discoverable
If you need Bluetooth on regularly (for earbuds, smartwatches, etc.), try switching your device to non-discoverable mode. That way, strangers won’t see your device when scanning for nearby Bluetooth connections.
Not all phones have this setting, so check your Bluetooth options. If it’s not there, just turn off Bluetooth when you’re not using it.
Reject unknown pairing requests
In most cases, a new Bluetooth device has to send a pairing request (and you have to accept it) before anything can be shared. So if you get a random request from a device you don’t recognize, just reject it.
Update your operating system and security settings
Keeping your software up-to-date is critical for computer and mobile security. Why? Because operating systems are not perfect. They sometimes have bugs, weaknesses, and vulnerabilities that hackers can exploit, including through Bluetooth. Updates help patch these vulnerabilities and often introduce helpful new security features.
Avoid clicking on suspicious Bluetooth messages
This tip won’t stop bluejacking attempts from showing up, but it’ll help keep you safe if one does.
If you get a strange message via Bluetooth, don’t click on it, especially if it includes a link. Even if it looks harmless, it could lead to a phishing site or trigger a hidden malware download.
Can a VPN protect you from bluejacking?
No, a VPN won’t protect you from bluejacking. That’s because VPNs are designed to secure internet traffic, not short-range wireless connections like Bluetooth. So even with a VPN enabled, if Bluetooth is turned on and your device is discoverable and within range of a malicious actor (or a prankster), they could still attempt a bluejacking attack.
That said, it’s still smart to use a VPN. It protects you against many other types of cyberattacks, especially the ones that are far more common and dangerous than bluejacking. After all, bluejacking isn’t the most serious digital threat out there. The attacker has to be physically close: Bluetooth range is typically around 33 feet (10 meters). With specialized equipment, that range can sometimes extend up to 330 feet (100 meters).
By contrast, attackers can target your devices more easily if you connect to public Wi-Fi without a VPN. On secure networks, the Wi-Fi password helps create a private connection between your device and the router, so others nearby can’t see your data. But public Wi-Fi networks often don’t have a password, so anyone nearby can intercept what you’re doing online, including sensitive info like passwords or bank details.
For most people, these kinds of online threats are a much bigger concern than bluejacking. A VPN helps defend against them by encrypting your internet traffic, so even if someone captures it, they won’t be able to read it. It also hides your IP address, making your activity, location, and private data much harder to track or intercept.
FAQ: Common questions about bluejacking
What is the meaning of bluejacking?
What is the purpose of bluejacking?
Is it possible to bluejack a phone?
Can someone access my data through bluejacking?
Can bluejacking happen on modern devices?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN