What is ChaCha20, and how does it work?

Every time you send a message, make an online payment, or log into a secure service, encryption is working behind the scenes to keep your data private. One of the algorithms doing this job today is ChaCha20: a fast, secure, and lightweight cipher trusted by tech giants and security experts alike. Here’s what it is and how it keeps your data safe.
Understanding the ChaCha20 algorithm
To understand the ChaCha20 algorithm, it’s helpful to break it down into its core elements: its origin, the process it uses to produce encrypted data, and the role of its key, nonce, and counter. Each of these parts works together to provide speed, efficiency, and security, making ChaCha20 a strong option in many modern encryption protocols.
Who developed ChaCha20 and why?
ChaCha was developed in 2008 by Daniel J. Bernstein, an American-German mathematician, computer scientist, and cryptographer. It’s based on his earlier design, Salsa20.
One of the main reasons for creating ChaCha20 was to provide a strong alternative to widely used ciphers like Advanced Encryption Standard (AES). While AES is very secure, it runs fastest on devices that support hardware acceleration: special CPU instructions, like Intel’s Advanced Encryption Standard New Instructions (AES-NI), which speed up its operations. Many older, mobile, or low-power devices don’t have this hardware support, making AES slower and more battery-hungry in software.
ChaCha20 was designed to avoid this problem. It uses only simple operations that run quickly on virtually any processor. This lightweight design makes it especially well-suited for smartphones, embedded systems, and other constrained environments. Today, ChaCha20 is recommended in modern protocols such as Transport Layer Security (TLS) 1.3 as a reliable option alongside AES.
How ChaCha20 works
Let’s say you wanted to encrypt this message using ChaCha20: “ExpressVPN protects my online privacy and helps keep my data safe.” Here’s how this is done, step by step.
1. Turn the message into bytes.
Computers work with bytes, which are 8-bit units that can store a number from 0 to 255. Text like our sentence is stored by mapping each character (“E,” “x,” space, “.”, etc.) to 1 byte. Our sentence is 66 bytes long, so it will take a little more than one 64-byte chunk (block) to encrypt.
2. Next, you need a secret key.
ChaCha20 is a symmetric cipher, which means the same secret is used to encrypt and decrypt. That secret is a 256-bit key (32 bytes). You can think of it as a long, random password that only the sender and receiver know. Why 256 bits? It’s large enough that guessing it by trial and error is effectively impossible.
3. You also need a nonce (number used once).
A nonce is a public, unique number chosen for each message you encrypt with a given key.
In the Internet Engineering Task Force (IETF) version of ChaCha20, the nonce is 96 bits (12 bytes). It doesn’t have to be secret, but it must never repeat with the same key. Reusing a key-nonce pair would reveal your message.
4. ChaCha20 makes a keystream.
ChaCha20 belongs to the “stream cipher” family. Instead of directly scrambling your message, it first produces a stream of pseudo-random bytes called a keystream. You then combine that keystream with your message bytes using a simple operation called exclusive OR (XOR) (step 7).
How does ChaCha20 make the keystream?
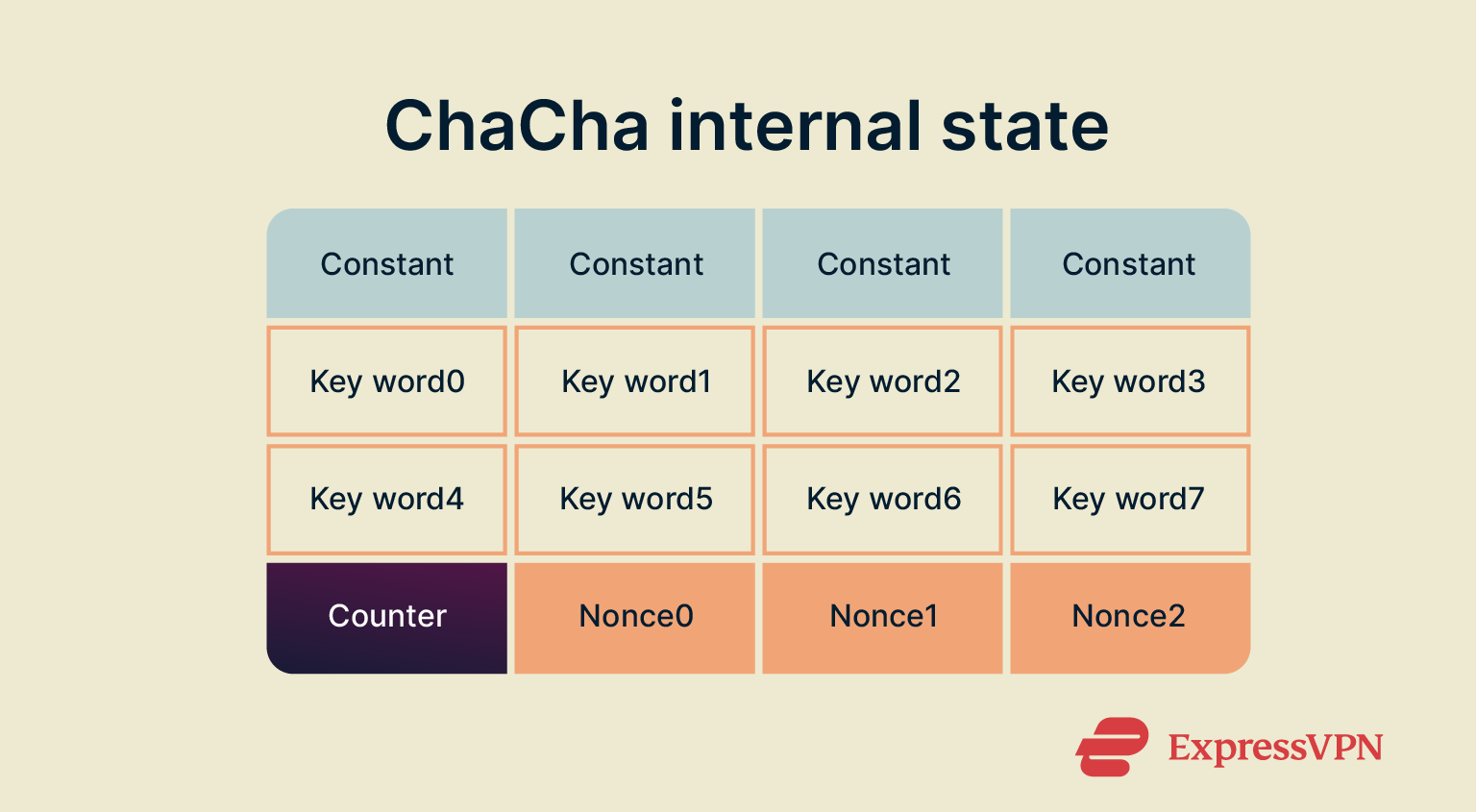
Build an internal state
ChaCha20 keeps a small working area called the state, arranged as a 4×4 grid of numbers. Each number in the grid is a word, which here means a 32-bit (4-byte) unsigned integer like, for example, 00000000 00000000 00000111 01001001.
The 16 words in the grid are filled with:
- 4 fixed constants (they just identify the algorithm),
- 8 words from the 256-bit key (since 8 × 4 bytes = 32 bytes),
- 1 block counter (explained next),
- 3 words from the nonce (3 × 4 bytes = 12 bytes).
The block counter
The keystream is produced in blocks of 64 bytes at a time.
To make each 64-byte block different, ChaCha20 uses a 32-bit counter inside the state that starts at 0 for the first block, 1 for the next block, and so on.
Mix the state (the ARX core)
ChaCha20 repeatedly mixes the 16 words from the grid using only three operations: addition (modulo 232), rotation (bitwise rotation of 32-bit words), and XOR (which compares two bits and outputs 1 if they’re different and 0 if they’re the same).
This mixing, based on Addition, Rotation, and XOR (ARX) operations, is done in rounds (ChaCha20 does 20 rounds). The takeaway is that these simple, fast operations thoroughly scramble the state in a way that’s hard to reverse without the key.
Produce 64 bytes of keystream
After the mixing, ChaCha20 adds the original state to the mixed state (word by word) and then outputs the result as 64 keystream bytes. That’s one keystream block.
5. Make as many keystream blocks as needed
Your message can be any length. ChaCha20 simply uses counter = 0 to make the first 64 bytes of keystream, counter = 1 for the next 64 bytes, counter = 2 for the next 64 bytes, and so on. Because the counter changes, each keystream block is unique (even with the same key and nonce).
6. Line up keystream with your message
Our example message is 67 bytes, so block 0 covers message bytes 0–63 (64 bytes), and block 1 covers message bytes 64–66 (the last 3 bytes). We only use the first 3 bytes from the second keystream block and ignore the rest.
7. Combine message with keystream using XOR
XOR is a per-byte operation with a neat property: doing the same XOR twice gets you back where you started:
Encryption (per byte): plaintext XOR keystream = ciphertext
Decryption (per byte, same keystream): ciphertext XOR keystream = plaintext
Comparing ChaCha20 with other ciphers
While ChaCha20 is widely used today, it’s not the only encryption algorithm in play. Other ciphers, like AES and Rivest–Shamir–Adleman (RSA), are also common, but they work in different ways and are suited for different tasks. Comparing them helps show where ChaCha20 fits in and why certain protocols choose it over the alternatives.
ChaCha20 vs. AES
ChaCha20 and AES are both symmetric key encryption algorithms, meaning the same key is used for both encryption and decryption. To better understand various cryptographic techniques, including the differences between encryption and hashing, you can check out this explanation of hashing vs. encryption.
The main difference between ChaCha20 and AES lies in how they process data. AES is a block cipher, encrypting data in fixed‑size blocks, while ChaCha20 is a stream cipher, generating a continuous keystream that’s combined with the data.
AES often benefits from hardware acceleration on modern processors, which makes it extremely fast in those environments. ChaCha20, on the other hand, is designed to perform consistently well even without specialized hardware support, making it a strong choice for mobile devices and low‑power systems. That’s why ExpressVPN uses both AES-256 and ChaCha20 for its Lightway protocol, automatically switching to the one best suited for your device (you can also choose one or the other manually).
Another practical difference is in implementation. AES can be more complex to code securely, as it may be vulnerable to timing attacks if not implemented carefully. ChaCha20 uses simple operations, ARX, that naturally run in constant time, helping reduce this risk.
Both ciphers are considered secure when properly implemented, and modern protocols like TLS 1.3 include support for each. The choice between them depends on the device’s hardware and performance requirements rather than on security concerns.
| Feature | ChaCha20 | AES |
| Type of cipher | Stream cipher | Block cipher |
| Hardware acceleration | Fast on all devices | Best with AES‑NI (dedicated hardware instructions) |
| Ease of implementation | Simpler, constant‑time operations | More complex, needs careful coding |
| Speed without AES‑NI (dedicated hardware instructions) | Very fast | Slower |
ChaCha20 vs. RSA
ChaCha20 and RSA aren’t direct competitors: they perform different functions in secure communication.
RSA is an asymmetric encryption algorithm, meaning it uses a key pair: one public and one private. It’s typically used at the start of a secure connection to exchange encryption keys or verify identities. In TLS, the symmetric-key algorithm is often AES, with the key exchange secured by RSA.
Because RSA involves more complex mathematics and operates on larger key sizes, it’s slower and less efficient for continuous data encryption.
ChaCha20, on the other hand, is a symmetric stream cipher. It uses a single shared key for both encryption and decryption, making it faster and better suited for ongoing data transfer.
In practice, many secure protocols combine both approaches: RSA (or another asymmetric algorithm) for the initial handshake and ChaCha20 or another symmetric cipher for the rest of the session.
Advantages of ChaCha20
ChaCha20 is popular not only because it’s secure but also because it works well in real‑world situations. It’s fast on all kinds of devices, even phones and gadgets with less power. Its design is straightforward, which helps avoid common mistakes that can weaken encryption.
Speed and performance on mobile and low-power devices
ChaCha20 is designed to work efficiently on all kinds of hardware, not just high‑end processors. On devices without AES hardware acceleration, such as many smartphones, tablets, or IoT devices, it can run noticeably faster.
Simplicity and resistance to timing attacks
ChaCha20 is built around simple operations: ARX. These run in constant time, meaning the execution speed doesn’t change based on the data being processed: all operations take the exact same time.
This design makes it easier to implement securely and helps protect against timing attacks, which try to extract information by measuring how long encryption steps take.
What are the known limitations of ChaCha20?
ChaCha20 has been studied for years, and no real‑world breaks of the full 20‑round version have been published. Overall, it’s the most thoroughly tested alternative to AES there is today. However, it has some clear limits that developers should keep in mind. Using it outside these boundaries can weaken its protection.
- Nonce reuse is a serious risk: Using the same nonce with the same key instantly breaks confidentiality. Each nonce–key pair must be unique.
- No built-in authentication: ChaCha20 only encrypts data. To check that data hasn’t been altered, it should be used with Poly1305.
- Limit on encrypted data per key/nonce: ChaCha20 can handle up to 2³² blocks of 64 bytes (about 256 GB) with the same key and nonce. Passing this limit would result in keystream reuse and completely undermine the security of the encryption.
ChaCha20-Poly1305 explained
ChaCha20‑Poly1305 is a pairing of two cryptographic components that work together to protect data:
- ChaCha20 encrypts information with a shared secret key, turning readable text into something that looks like random data to anyone without the key. However, it doesn’t detect tampering.
- Poly1305 produces a message authentication code (MAC) that lets the receiver confirm the data hasn’t been altered and that it came from the right source.
Together, they form what’s known as Authenticated Encryption with Additional Data (AEAD). This means the encryption process not only hides the contents of the message but also verifies its integrity.
Poly1305 isn’t the only option, but it’s the most common choice when ChaCha20 is used in modern protocols. That’s because ChaCha20-Poly1305 has been standardized by the IETF (RFC 8439) and is widely supported in TLS, SSH, WireGuard, and other protocols, so it’s the de facto standard.
ChaCha20 in 2025: Where it’s used in modern systems
ChaCha20 has become a standard choice in many security‑focused applications. In internet security, it’s used in TLS connections, often together with Poly1305, to protect HTTPS traffic, especially on devices that don’t have hardware support for AES. Major browsers like Chrome and Firefox, and web servers such as nginx and Apache, support this cipher suite.
It’s also widely used in virtual private networks (VPNs). The WireGuard VPN protocol, for example, sets ChaCha20‑Poly1305 as its default to secure data while keeping performance high on mobile and embedded devices. Support is also built into major operating systems, including Linux, Android, iOS, and Windows.
FAQ: Common questions about ChaCha20
Does Google use ChaCha20?
Yes. Google adopted ChaCha20 with Poly1305 in 2014 as part of its Transport Layer Security (TLS) / Secure Sockets Layer (SSL) protocols. The goal was to improve performance and security for mobile devices and servers that lack Advanced Encryption Standard (AES) hardware acceleration, making secure connections faster and more efficient in those environments.
Is ChaCha20 quantum-resistant?
Yes. Symmetric ciphers, like ChaCha20, are generally regarded as quantum-safe, provided they use sufficiently long keys (e.g., 256 bits).
Can ChaCha20 be used for file encryption?
Yes. ChaCha20 can be used in file encryption tools to protect sensitive data stored on devices. Its speed and efficiency make it suitable for both large files and devices with limited processing power.
Can ChaCha20 be cracked?
There are no published real‑world attacks that break the full 20‑round ChaCha20 cipher. Security experts continue to study it, and when used correctly within its limits, it is considered secure for modern encryption needs.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN