How does the internet work?

Billions of people use the internet daily for everything from work to shopping, banking, entertainment, and keeping in touch with family and friends. It’s an integral, essential part of everyday life, yet many people wouldn’t be able to explain, in detail, how it all works.
If you’ve pondered the question “How does the internet work?” then this guide is here to break it all down. We’ll cover the physical infrastructure, how data travels through the internet, how devices connect, the governance structure of the internet, and more.
What is the internet?
Before we dig into the details, let’s begin with the basics and provide a clear definition of what the internet actually is.
Definition and history
At its core, the internet is a network. A network is a group of connected devices that can send data to each other, and the internet is sometimes called the “network of networks” because it’s a vast, sprawling collection of computer networks that can all interconnect (hence the name “internet” or “interconnected network”).
While people tend to think of the internet as a modern innovation, its history dates back several decades. In the 1960s, a U.S. military project called the Advanced Research Projects Agency Network (ARPANET) connected computers at research institutions on the same network. This was essentially a very primitive version of the internet we know today.
In the decades that followed, networking architecture and technology evolved a great deal. Communication protocols were developed to control how data moves between devices, and other pieces of internet infrastructure, like the Domain Name System (DNS), were developed, paving the way for what was to come.
The 1990s brought the invention of the world wide web and web browsers. The internet opened up for commercial use, with the first of countless websites being created. Since then, internet technology has evolved massively, with faster speeds, more stable connections, widespread accessibility, and more diverse devices, like phones and smart home gadgets, coming online.
Key components and structures
The internet relies on a vast and complex collection of physical and digital infrastructure, including fiber-optic cables, routers, modems, data centers, switches, protocols, and software. All of these elements have their part to play in the greater collective, facilitating the flow of data and stable connections between devices worldwide.
How the internet works step by step
Let's examine how the internet's various systems and components work.
How data travels through the internet
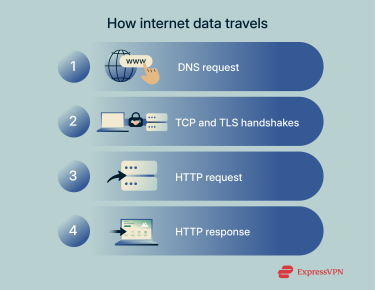 At its core, the internet is all about data and how it flows from device to device and network to network. The steps below show how data travels across the internet in a typical user interaction:
At its core, the internet is all about data and how it flows from device to device and network to network. The steps below show how data travels across the internet in a typical user interaction:
- Domain Name System (DNS) request: First, when you want to access any sort of online service (like typing a web address into your browser), your device sends a DNS request to the system.
- Handshakes: The request is processed to find the exact Internet Protocol (IP) address you wish to contact, and two handshakes take place. The first is a Transmission Control Protocol (TCP) handshake, which establishes a connection between the user and the IP address. The second, which only occurs on Hypertext Transfer Protocol Secure (HTTPS) sites, is a security-oriented Transport Layer Security (TLS) handshake, which authenticates the client and server and encrypts data between the two so that attackers can’t see or intercept the data they exchange.
- Hypertext Transfer Protocol (HTTP) request: Once the handshakes have taken place and a secure connection is established, your browser submits an HTTP request to ask for specific pieces of internet data, like the text and images that make up this webpage, for example.
- HTTP response: The server processes the request, finds the relevant data, breaks it down into individual data packets, and delivers it back to the user.
Packets and packet switching
As mentioned above, data on the internet travels in the form of packets. These packets are transmitted across the internet over fiber optic cables, modems, and other infrastructure, passing through routers to reach their destination. Each packet is assigned a specific destination address so it can be routed independently wherever it needs to go, following the most efficient path available at the time. This process is known as packet switching.
To ensure that data arrives correctly and can be reassembled into its original form, each packet also includes header information such as the source and destination IP addresses, and in protocols like TCP, a sequence number. This enables receiving systems to verify that packets arrive intact and in the correct order.
The role of protocols
Protocols are like rules or frameworks for how data should be transmitted across the internet. They set out the processes and standards for how data is formatted, sent, received, processed, and managed. TCP, for example, provides a framework for safe data transmission, while HTTP controls how data is formatted between web servers and browsers.
The role of DNS
DNS stands for the Domain Name System. It’s sometimes referred to as the “internet’s phone book,” and its main role is to translate human-readable text-based web addresses, like www.example.com, into the numerical IP addresses that devices use when communicating with each other.
How devices connect to the internet
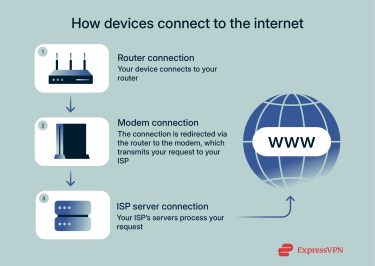 Devices like computers and smartphones connect to the internet through this three-step process:
Devices like computers and smartphones connect to the internet through this three-step process:
- Router connection: First, your device connects to your router, which essentially bridges the gap between devices like computers and phones and the internet. It uses the Dynamic Host Configuration Protocol (DHCP) to assign a unique private IP address to your device within your local network. Note that when your device accesses the internet, the router uses Network Address Translation (NAT) to translate your private IP into its public IP address, allowing communication with external websites and services.
- Modem connection: The router sends internet traffic to the modem, which connects your local network to your internet service provider (ISP). The modem’s job is to modulate and demodulate signals; it converts digital data from your network into a transmittable form suitable for your ISP’s infrastructure, and vice versa.
- ISP server connection: In the final stage of establishing an internet connection, your data arrives at your ISP’s servers, which process your device’s request and form a connection with the internet. From that point, you can submit queries via your web browser or other software to access internet data.
Wireless and internet access alternatives
Most devices now connect to routers wirelessly, through Wi-Fi technology. This involves the use of radio signals to transmit data between a router and a wireless adapter built into a computer or another device. There are also other internet access alternatives, such as satellite internet, which uses networks of low Earth orbit (LEO) or geostationary satellites to transmit data to homes and businesses.
Difference between the internet and the web
The internet and the world wide web, or just “web” for short, are terms you may hear used interchangeably. However, while they’re closely related, they’re not the same thing.
The easiest way to differentiate between the two is to see the web as a service and the internet as the infrastructure that powers that service. The internet is a vast, global network of connected devices and other infrastructure that allows data to travel between devices. The web is the collective term for the countless websites and webpages that you can access on the internet via web browsers.
Physical infrastructure of the internet
Internet infrastructure is divided into two main categories: physical and digital. Digital infrastructure relates to the software side of the internet, such as protocols, but without the physical infrastructure, like cables, routers, and servers, none of the software would function.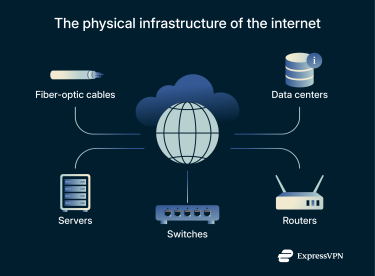
Internet backbone
The so-called “internet backbone” refers to the core pieces of physical infrastructure that do most of the “heavy lifting” to keep the internet up and running.
This includes the countless miles of high-capacity fiber optic cables that stretch out across the world and along the ocean floors, transmitting extraordinary amounts of internet data every second in the form of light pulses.
Other elements of the internet backbone include Ethernet cables connecting physical devices to routers, plus data centers that store the vast amounts of data that users access online, and the routers and switches that control the flow of that data.
Routers are responsible for forwarding data to and from the internet; for example, your home Wi-Fi router is what allows you to connect your various devices, like your computer, phone, and smart TV, to the internet. Switches, on the other hand, operate within a local network. They connect multiple devices such as computers, printers, and access points so they can communicate with one another. They forward Ethernet frames between devices using Media Access Control (MAC) address tables to ensure each frame reaches the correct destination.
The broader concept of packet switching underlies how data moves across the internet as a whole, dividing information into small packets that travel independently along the most efficient paths to their destination.
Web servers and clients
Web servers and clients sit at opposite ends of internet communications, forming what is known as the client-server model.
A web server is a device or piece of software that stores and processes internet data, like webpages, images, or HTML code, in response to requests from clients. The clients, meanwhile, are the devices or pieces of software, such as web browsers, that send requests to servers.
When you visit a website, you take part in the client-server model of internet communications. You type a web address into your browser and hit “Enter.” At that point, your browser, or web client, sends a request into the system, where the relevant web server receives it, processes it, and sends the data you want back to your device.
The importance of bandwidth
Bandwidth is an important concept to understand. It refers to the maximum amount of data that can be transmitted over a network connection, and it’s usually measured in megabits per second (Mbps) or gigabits per second (Gbps). The bigger the bandwidth, the more data can flow.
Therefore, bandwidth directly influences your download and upload speeds and your overall experience when using the internet to browse the web, stream, download files, or work. Higher bandwidth is vital for more data-heavy activities or networks with many devices, but more bandwidth often comes at a higher cost due to the high-capacity infrastructure needed to provide it.
Internet governance and control
A system as complex and far-reaching as the internet demands careful control, and there are multiple tiers of internet governance, with numerous bodies and regulators overseeing it all.
Who controls the internet?
There’s no singular authority or institution that controls the whole internet. Instead, a vast range of regulatory bodies, service providers, infrastructure owners, and even governments influence the way it works around the world.
Internet regulation bodies
These are the organizations and regulatory groups that manage some of the core functions and systems of the internet. They include:
- Internet Corporation for Assigned Names and Numbers (ICANN): This organization manages domain names and the allocation of IP addresses.
- Internet Assigned Numbers Authority (IANA): This body operates as part of ICANN and performs the IANA functions, which include coordinating the DNS root zone, managing IP address allocations to regional internet registries, and maintaining key internet protocol parameters.
- Internet Engineering Task Force (IETF): This organization is responsible for many of the most important internet and networking standards, such as TCP, IP, and HTTP.
Impact of legislation on internet use
Lawmakers in countries around the world also influence the way the internet works. For example, the European Union established the General Data Protection Regulation (GDPR) in 2018, giving internet users more control of their personal data and requiring companies to be more transparent about how they collect and use it.
International governments also regularly debate internet issues, like net neutrality, and establish laws regarding data protection, cybersecurity, and cybercrime.
The role of internet service providers
Internet service providers (ISPs) are the companies that give everyday users and businesses access to the internet. They operate the infrastructure that delivers service directly and connect to other networks through peering, transit agreements, and internet exchange points (IXPs).
ISPs may also implement traffic management practices to maintain network performance, comply with regulations, or enforce their terms of service. These practices help ensure data can flow efficiently and networks remain reliable for all users.
Security and reliability of the internet
 While the internet offers countless opportunities and benefits, it also brings risks. Many pieces of core internet infrastructure are not inherently secure, like the DNS, for example, which sends queries in plaintext by default. Because of this, cybercriminals can exploit weaknesses within the infrastructure, launching cyberattacks to steal people’s data, money, and even their identities.
While the internet offers countless opportunities and benefits, it also brings risks. Many pieces of core internet infrastructure are not inherently secure, like the DNS, for example, which sends queries in plaintext by default. Because of this, cybercriminals can exploit weaknesses within the infrastructure, launching cyberattacks to steal people’s data, money, and even their identities.
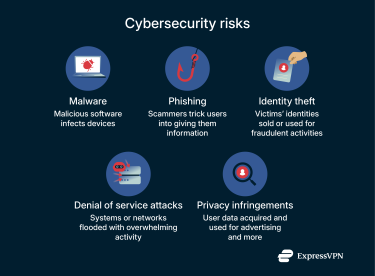
Cybersecurity risks
- Malware: Malicious software like viruses can infect devices, impacting their performance and putting users at risk. Certain malware programs can, for example, allow cybercriminals to spy on users or control their devices remotely.
- Phishing: Phishing and other social engineering attacks involve scammers tricking, coercing, or otherwise deceiving users into giving up their data, like login credentials for their online profiles.
- Identity theft: A main aim of some cyberattacks is to steal the victim’s identity, taking important pieces of their personal information, such as their Social Security number, to sell on the dark web or use for fraudulent activities.
- Denial of Service (DoS) attacks: One of many types of cyberattacks, DoS attacks involve target systems or networks being flooded with traffic or requests, overwhelming their resources and potentially taking them offline.
- Privacy issues: Various entities, both legitimate and illegitimate, can use an array of techniques to acquire internet users’ data and either sell it or use it for advertising and other purposes.
Importance of TLS and HTTPS
The internet has progressively become more secure, thanks to security protocols like Transport Layer Security (TLS) and Hypertext Transfer Protocol Secure (HTTPS).
TLS helps secure online communications by encrypting data and carrying out authentication processes between clients and web servers, keeping online data safer and more private. Users can tell if a site uses TLS by looking at its URL; if it begins with “HTTPS,” then that means the site uses TLS.
Protecting yourself online
Given the vast number of evolving online threats and the potentially severe consequences for victims, everyday users need to take care when using the internet. Fortunately, there are plenty of tools and techniques available to help you enjoy the web while staying relatively safe.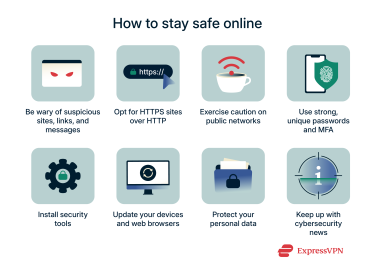
Tools and best practices for safe browsing
- Be cybersecurity aware: There are many fake and fraudulent websites out there, along with cybercriminals who will use all tools at their disposal to trick victims and steal their data. Be aware of the risks and be cautious when browsing. Look out for misspelled URLs, suspicious email attachments, and messages from unrecognized senders.
- Check for HTTPS before you share: Most major websites use HTTPS, which encrypts data between your browser and the site. If a site uses plain HTTP, avoid entering sensitive information like passwords, credit card numbers, or personal details.
- Take care on public Wi-Fi: Public Wi-Fi hotspots in places like cafés, airports, and hotels can be convenient for getting online when you’re on the move, but they can also put your data at higher risk of theft or interception. When using the internet in public, always use a virtual private network (VPN) to protect your data and avoid accessing sensitive accounts.
- Use strong passwords and multi-factor authentication (MFA): Use unique, long, and complex passwords for all of your online accounts to minimize the risk of unauthorized access, and enable extra protective layers, like MFA, wherever possible. Consider using a password manager like ExpressVPN Keys to help you create and store secure passwords.
- Invest in security tools and extensions: There are numerous helpful security tools and browser extensions you can install to stay safe online, including tracker blockers like ExpressVPN Threat Manager, as well as antivirus programs and VPNs (more on those below).
- Keep your devices and browsers updated: Many cyberattacks work by exploiting weaknesses in operating systems or browser software, but developers regularly release updates to fix those weaknesses. By keeping your devices and software up to date, you’ll make it harder for criminals to target you.
- Protect your personal information: While there are many situations where you need to provide personal information online, like when buying a product or setting up an account, it’s wise to be cautious about what you share and who you share it with. Make sure you only give away necessary information to trusted, official entities.
- Learn about emerging threats: Improve your cybersecurity knowledge and stay up-to-date with the latest threats by reading about them on technology or security blogs and websites. This way, you’ll be aware of new attack methods and protection strategies ahead of time, so you can take a more proactive approach to online safety.
How VPNs protect your privacy and data
A virtual private network (VPN) is a tool that can help protect your privacy and secure your data when using the internet. A VPN creates a secure, encrypted tunnel between your device and the VPN server, so your internet traffic is protected from potential eavesdroppers.
By routing your connection through the VPN server, a VPN also hides your IP address, making it harder for websites and third parties to track your location or link your activity to you.
VPN vs. antivirus vs. firewalls
VPNs form part of a trio of crucial cybersecurity tools, alongside antivirus software and firewalls. None of these elements is inherently better or more important than the others, as they all serve distinct purposes.
As described above, VPNs encrypt connections and hide your IP to help you use the internet more privately. Antivirus software detects and removes malicious software, while firewalls monitor traffic in and out of your network to help block unauthorized access and malicious traffic.
Emerging internet trends
The internet is always evolving, with new technologies, protocols, and trends changing the way we use and enjoy it and expanding its capabilities. Here are some of the most significant developments in recent years:
- AI: AI is becoming a big part of the online experience, with AI-powered search engine results, chatbots, and generative AI tools shaping the way people interact with, learn from, and work through the internet.
- Internet of Things (IoT): The IoT continues to expand and diversify, with an increasing array of smart devices, like smart home appliances, capable of connecting to the internet to send and receive data. This unlocks new possibilities and features for devices that have previously lacked connectivity.
- Edge computing: To minimize latency and optimize connection speeds, modern networks are increasingly investing in edge computing. This revolves around moving data processing and storage physically closer to the locations where it’s used or made, instead of having it in centralized clouds or data centers.
- 5G and beyond: We’ve seen the progression of mobile data from 3G through to 5G, which is faster than anything before. Testing and initial launch of 6G technology are on the horizon and are set to supercharge mobile networks and smart city infrastructure.
- Next-level cybersecurity: As the internet evolves, so, too, do the tools that cybercriminals can use to target their victims. For this reason, cybersecurity is also evolving and is largely moving towards zero-trust models, embracing AI and other technologies for continuous authentication and next-level data protection.
FAQ: Common questions about the internet
Where is the internet physically located?
The internet doesn’t have any fixed physical location. It exists across a vast network of physical infrastructure that extends across the globe, including computers, servers, data centers, internet exchange points, and countless miles of fiber optic cables.
What keeps the internet running?
The core infrastructure of the internet, sometimes referred to as the internet backbone, is largely what keeps the whole system as we know it up and running. This includes servers, routers, data centers, fiber optic cables, and more.
Does the internet work without Wi-Fi?
Yes, while Wi-Fi is the most common and popular option for connecting to the internet wirelessly, it’s not the only connectivity technology in existence, and users can still connect to the internet without Wi-Fi. They can use alternative methods, like Ethernet connections, for example.
What are internet protocols?
Put simply, internet protocols are like rule sets or frameworks that allow devices to communicate and exchange data across the internet. They control how data is formatted, transmitted, and received. Important examples include the Internet Protocol (IP) and the Transmission Control Protocol (TCP).
How do ISPs manage internet traffic?
Internet service providers (ISPs) receive requests from users’ modems at their data centers. ISP servers then process those requests, forwarding them on through relevant devices to find the selected web server and returning the requested content to the user’s devices.
What is a modem and a router?
The modem is the device that brings internet service into the home from the internet service provider (ISP), while the router is responsible for delivering the connection onward to devices within the home, like computers and phones.
How can I improve my internet speed?
Some ways to enhance your internet speed are to consider alternative internet service providers and higher-speed plans, make sure your devices and browsers are always up-to-date, upgrade your router to a more recent, advanced model, and consider using a wired connection.
What is the role of cybersecurity in the internet?
Cybersecurity refers to the various tools, technologies, and best practices users can employ to protect their devices and data from cyberattacks. It’s a vital concept for safe and reliable use of the internet, as there are many digital threats out there.
Do I need a VPN to stay safe online?
Many cybersecurity experts recommend using a VPN. It will encrypt your internet traffic and hide your IP address, making it much more difficult for third parties to intercept your data or target you with cyberattacks. However, it doesn’t replace basic cybersecurity practices like using strong passwords, keeping software updated, and avoiding suspicious links. A VPN is a helpful tool for extra security, especially on public Wi-Fi, but it’s just one part of staying safe online.
How does a VPN differ from HTTPS encryption?
Both VPNs and HTTPS relate to encryption, but a VPN will encrypt all of your internet traffic and hide your IP address from all the internet sites you visit. HTTPS, meanwhile, only encrypts data between your browser and specific websites.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN