Hacktivism: What it is and how it works

Hacktivists combine technology and activism, using digital tools to seek political or social change, often by challenging institutions. However, their actions raise difficult questions about legality, ethics, and real-world impact.
This article explores the tactics, motivations, and controversies surrounding hacktivism, and the blurred line between digital protest and crime.
What is hacktivism?
Hacktivism is a portmanteau of the words “hack” and “activism,” and it refers to the use of hacking skills to promote social, political, or ideological causes. Essentially, it’s a form of protest carried out in the digital world.
How does hacktivism work?
Hacktivists use hacking techniques to send a message, draw attention to a cause (hack-for-a-cause strategy), and/or respond to what they perceive as injustice.
For example, a hacktivist may target a government or corporation they believe to be corrupt by launching distributed denial-of-service (DDoS) attacks to disrupt services, defacing websites, or leaking stolen data.
Common methods used in hacktivism
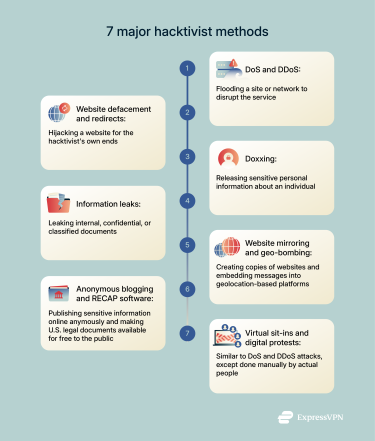
Denial-of-service (DoS) and distributed DoS (DDoS) attacks
DoS and DDoS attacks involve deliberately overwhelming a website or network with automated server requests, leading to the slowdown or shutdown of the service.
When the attack is launched from a single source, it’s a DoS attack. If the perpetrator uses multiple sources, usually a botnet (network of compromised devices), to perform the attack, it’s called a DDoS attack.
Website defacement and redirects
Website defacement is when a hacktivist alters the content and media on a website. Sometimes this involves replacing it with messaging that reflects the hacktivist’s point of view. In other cases, the aim may be to embarrass or challenge the target.
A website redirect is very similar in the sense that it’s a method where the hacktivist hijacks the target’s website for their own ends. Instead of altering the original website, though, redirects send visitors to a different site entirely, usually one that contains information or messaging supporting the hacktivist’s cause.
Doxxing
Doxxing involves compiling and releasing sensitive personal information about an individual, such as their address, phone number, email, or even family details, with the goal of shaming, intimidating, or harassing them.
Ordinary people can become the victims of doxxing as well. This is why it’s important to take measures to protect yourself from doxxing by limiting the amount of publicly available information about you and strengthening your account passwords. Using a virtual private network (VPN) when you're online can also help by hiding your IP address and your location.
Information leaks
This method is very similar to doxxing. However, it usually targets organizations, such as governments and corporations, rather than individuals. It involves leaking internal, confidential, or classified documents, usually to reveal misconduct, corruption, or abuses of power.
Website mirroring and geo-bombing
Hacktivists sometimes create copies (“mirrors”) of websites so that people can access content that’s been censored or taken down. This method is used to counter attempts to suppress information, such as politically sensitive material, whistleblower documents, or restricted news.
Geo-bombing is another method that hacktivists use to raise awareness or bypass censorship. It involves uploading geotagged content containing messages related to their cause so that it appears on location-based platforms (such as Google Maps or Google Earth) and location-based search results.
For example, a hacktivist might upload a video drawing attention to alleged human rights abuses, ensuring that it appears when users explore or search within that specific location.
Anonymous blogging and RECAP software
Anonymous bloggers publish sensitive information online while hiding their identity to escape potential retaliation. They’ll typically use tools like Tor, VPNs, or secure blogging platforms for this.
RECAP is an example of anonymous blogging. In the U.S., many legal documents are stored behind paywalls in a system called Public Access to Court Electronic Records (PACER). So hacktivists created a browser extension called RECAP that automatically saves court documents that have been downloaded from PACER and uploads them onto RECAP, where they’re available for free.
Virtual sit-ins and digital protests
Virtual sit-ins are kind of like DoS and DDoS attacks, in that the goal is to disrupt a target website by flooding it with a lot of traffic or requests. The difference is that virtual sit-ins are done “manually” by actual people (and not by bots or scripts), coordinating their efforts to achieve the same effect.
Types of hacktivism
Political hacktivism
Political hacktivism is typically a response to perceived injustice or government overreach and aims to disrupt operations, expose wrongdoings, or raise awareness of political causes. For example, a political hacktivist may organize a virtual sit-in on a government website to protest a controversial policy.
Social justice and human rights hacktivism
Social justice and human rights hacktivism seek to challenge perceived injustices, promote equality, and protect civil liberties. For example, a hacktivist may use anonymous platforms or public archives to raise awareness about ongoing social issues.
Anti-corporate hacktivism
Anti-corporate hacktivism targets perceived corporate misconduct, such as poor wages, unsafe working conditions, or violations of consumer privacy. For example, a hacktivist might disrupt a company’s digital presence to draw attention to these issues.
Whistleblower-focused hacktivism
This type of hacktivism focuses on enabling individuals to share internal information anonymously, often in response to perceived misconduct. For example, a hacktivist might create or maintain secure dropboxes to protect the identity of whistleblowers.
Nationalist or ideological hacktivism
This type of hacktivism is driven by strong loyalty to specific beliefs, values, or identities (such as a nation or an ethnic community) and aims to promote or bring attention to that ideology. For example, a hacktivist might use geo-bombing to share content aligned with national sentiment.
Environmental hacktivism
Environmental hacktivism focuses on raising awareness of environmental issues and calling attention to environmentally harmful practices. For example, some hacktivists might launch DoS or DDoS attacks to protest the operations of companies linked to environmental harm.
Who are the hacktivist groups?

Anonymous
This hacktivist group originated on the site 4chan, where users are assigned random numbers to post anonymously, which is why they are colloquially referred to as “Anons.” And their members are easily recognizable thanks to their adoption of Guy Fawkes masks, inspired by the graphic novel and film V for Vendetta, as an identifying symbol.
Anonymous rose to prominence for its campaigns against high-profile targets, including the Westboro Baptist Church, the Church of Scientology, PayPal, Sony, and MasterCard. The group is still active today.
LulzSec
LulzSec was a short-lived hacktivist group active from May to June 2011. LulzSec was founded by members of another group known as Internet Feds, and its name is a portmanteau of “lulz,”a play on the term “lol,” and “sec,” which is short for security.
This group’s main motivation seemed to be causing as much disruption as possible, often described as “for the lulz.” It became known for its mocking tone, using slogans like, “Laughing at your security since 2011!”
It claimed responsibility for several high-profile attacks, including taking the CIA website offline, hacking the network of Bethesda Game Studios, and hacking servers for Sony Pictures.
WikiLeaks
Started in 2006 by Julian Assange, WikiLeaks is perhaps the most well-known hacktivist group internationally. It specializes in the collection and dissemination of “censored or otherwise restricted official materials involving war, spying, and corruption.”
Since its inception, WikiLeaks has made headlines internationally for its high-profile leaks involving world governments.
In 2019, Julian Assange was arrested by British authorities and held in Belmarsh prison for over 5 years while fighting extradition. He was released in 2024 after reaching a plea agreement with U.S. authorities.
WikiLeaks is no longer active today; it hasn't released any leaks since 2019, and 2021 was the last time that anything was published on its website.
Who do hacktivists target?
Unlike cybercriminals, who are less discriminating about who they target, hacktivists typically target powerful individuals or organizations.
Governments
Hacktivists sometimes target governments to express dissent or draw attention to political issues. For example, in 2011, Anonymous launched cyberattacks during political unrest in Tunisia.
Corporations
Corporations are often targeted due to alleged unethical business practices, environmental irresponsibility, or labor exploitation. For example, in 2011, LulzSec targeted Sony Pictures, which the group described as being “evil” in its messaging.
Religious institutions
Religious institutions are sometimes targeted by hacktivists who oppose their practices and policies, whether from a social justice or ideological standpoint. They might also be targeted by hacktivists who believe that they exert undue influence in politics and society.
Media outlets
Given the importance of media outlets in shaping public opinion, they can be attacked by hacktivists who disagree with their coverage (or lack thereof in countries where censorship is prevalent). For example, in 2013, a hacktivist group called the Syrian Electronic Army took down The New York Times website for criticizing the Syrian government.
Powerful individuals
Hacktivists sometimes focus on powerful individuals, like politicians, corporate executives, and even celebrities, instead of organizations. For example, in 2010, U.S. politician Sarah Palin’s website was hit by a DDoS attack for her stance against WikiLeaks. The attack was attributed to Anonymous.
Is hacktivism a form of hacking or activism?
Differences between hacking and hacktivism
Hacking refers to the use of technical skills to gain access to computer systems, networks, or digital devices. Hacktivism is the use of hacking techniques to promote political or social change.
This differentiates hacktivists from cybercriminals (also known as “black hat hackers”), who break into systems illegally for personal gain, and from “white hat hackers,” who use their skills ethically to help organizations strengthen their cybersecurity.
Hacktivism vs. cyberterrorism
Both terms are imprecise. But generally, when people say “hacktivism,” they’re referring to actions that they believe fall under the umbrella of digital protest and civil disobedience with neutral to positive connotations. And when people say “cyberterrorism,” they’re referring to the use of hacking skills to coerce, intimidate, or incite panic, with exclusively negative connotations.
However, both hacktivists and cyberterrorists can claim to act for social, political, religious, or ideological reasons, and the activities of both groups can be greatly disruptive and cause harm, whether bodily, psychological, or financial.
For example, the U.S. government condemned the hacktivist group WikiLeaks for leaking classified military documents on the Afghan and Iraq wars, stating that the disclosures may “endanger the lives of Americans, our partners, and local populations who cooperate with us.”
Legal and ethical considerations
While the motivations behind hacktivism may be ethical, earning some hacktivist groups the support of the public, the methods used often violate the law.
Can hacktivism be justified?
The question of whether hacktivism can be justified is heavily subjective. Supporters will argue that it’s a tool for holding powerful institutions and individuals accountable, especially when traditional forms of protest and resistance are ineffective. But critics point out that it undermines the rule of law and can cause collateral damage.
Does hacktivism make a real-world impact?
Awareness-raising vs. real change
Hacktivism can be quite successful at raising awareness about social or political issues, as hacktivists’ activities make headlines and trend on social media. But this doesn’t always translate into meaningful action or reform, which requires sustained follow-up through legal channels. For this reason, hacktivism is sometimes seen as being performative or short-lived.
Media perception and public opinion
Portrayal of hacktivism in the media is very mixed. Some outlets laud hacktivists as digital Robin Hoods, while others frame them as reckless criminals or cyberterrorists.
Public opinion is equally divided. Support for hacktivism is high in cases where the target is already widely disliked but declines swiftly when perceived innocent parties experience harm or disruptions.
FAQ: Common questions about hacktivism
Is hacktivism legal or illegal?
Hacktivism often involves illegal activities, such as accessing private systems and data or causing service disruptions. This is why most hacktivists remain pseudonymous: they're identified only by a pseudonym (a fake name), like the hacktivist group known only as Anonymous. But not all hacktivism is illegal. Virtual sit-ins, for example, fall into a legal grey area where participants may be protected by free speech laws in countries that have them.
Is hacktivism considered ethical?
It’s complicated. Supporters see it as a form of digital civil disobedience and the only way to hold some powerful institutions or individuals accountable. Critics argue that it undermines the rule of law, lacks accountability, and causes collateral damage.
Is hacktivism considered cyberterrorism by law?
It’s unclear and can vary on a case-by-case basis. This is because "hacktivism" and "cyberterrorism" are both poorly defined terms, and whether an action is hacktivism or cyberterrorism depends heavily on subjective interpretation.
What tools and techniques do hacktivists use?
Hacktivists use a wide range of often controversial or illegal tools and methods to accomplish their goals, including distributed denial-of-service (DDoS) attacks, website defacement, doxxing, data leaking, anonymous blogging, geo-bombing, virtual sit-ins, and more.
What type of hacker is a hacktivist?
Whether a hacker is a hacktivist or not depends on their intent. A hacktivist claims to act for ethical reasons, usually to influence social or political change. On the other hand, black-hat hackers typically act for personal gain, usually with a financial motive.
Can anyone become a hacktivist?
Theoretically, yes, anyone can become a hacktivist, so long as they have the technical skills and a strong political or social conviction. However, participating in hacktivism carries serious legal and ethical risks. Hacktivist actions can break laws, violate terms of service, or cause unintended harm, even if the intent is political or social. It's a complex, controversial space that’s not without consequences.
Who investigates hacktivist activity?
It can vary widely, but generally speaking, since hacktivism often involves illegal activities, it’s investigated by law enforcement agencies. Government intelligence or cybersecurity divisions may become involved if government systems or critical infrastructure are targeted. And sometimes, private cybersecurity firms may be called upon to assist.
Is hacktivism a form of digital protest?
Yes, hacktivism is often considered a form of digital protest. The goal of hacktivist activity is typically to make a statement, raise awareness, or challenge what the hacktivists see as unjust institutions or individuals. That said, depending on who you ask and how you look at it, hacktivism can sometimes be considered a form of cyberterrorism instead.
How does public opinion view hacktivism?
Public opinion on hacktivism is mixed. Some people see hacktivists as whistleblowers or digital activists who challenge powerful institutions. Others view hacktivists as criminals, vigilantes, or reckless idealists, depending on the methods used and the impact of their actions.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN