What is a P2P VPN, and how does it work?

When you use a virtual private network (VPN), you’re trusting a company’s app and servers to protect your data. A peer-to-peer (P2P) VPN challenges that model with a different idea: what if the users are the network?
In this decentralized system, your traffic is routed through other participants, also known as peers, and your connection is used in return. However, this approach can introduce unique security, privacy, and even legal risks, depending on the quality of the network and who else is using it.
This guide explores how a P2P VPN works, what you need to consider before using one, and why a quality commercial VPN is generally a better choice.
What is a P2P VPN?
With a P2P VPN, each node or connection, such as a router, printer, network switch, or computer, connects directly with the others to share resources, such as files, data, or processing power.
Unlike a standard commercial VPN that uses a client-server model, a P2P network doesn’t necessarily have a central entity controlling the network. In this architecture, every participant is a peer who can potentially act as both a client (a consumer of resources) and a server (a provider of resources).
This means that instead of connecting to a server owned by a single company, users connect to one another, sharing resources like bandwidth and their IP addresses to create the network.
Of course, this means that the performance and security of your connection can be highly variable, as you’re depending on the functionality and trustworthiness of every other node. With a reputable commercial VPN like ExpressVPN, on the other hand, you get centrally maintained RAM-only servers and an audited no-logs policy that ensures none of your data is collected and stored.
How a P2P VPN works
In a commercial VPN, your device connects to a server owned and managed by the VPN company. A P2P VPN, on the other hand, runs on user-operated nodes. Every participant functions as a node, and your internet traffic is encrypted and routed through other users. Depending on the business model of the P2P VPN, your bandwidth and IP address are made available to route traffic for others in a continuous, reciprocal exchange of resources. This can introduce additional security and privacy risks.
Some systems route your traffic through several peers in sequence, adding a layer of encryption at each hop (this is called multi-hop or onion routing). Others use a single encrypted hop to an exit node. In either setup, the websites you visit see the exit node’s IP address, not yours. You function as a client by default and only become a relay or exit node if you install and run the required software.
The technology behind P2P
For a client to join a P2P network, it must first find other peers. This can be done using several methods, including:
- Distributed hash table (DHT): This works like a collaborative index for a global library. No single participant holds the entire index; instead, each holds a small piece and knows exactly where to direct queries to find a specific resource. This structure allows your client to locate other users efficiently without a central coordinator.
- On-chain directory: In this model, nodes register on a blockchain so clients can look up providers in a decentralized, auditable ledger (think a public registry rather than a single company-run directory). This records identities, reputation, and metadata on chain.
In either case, once you make these initial connections, the broader network reveals itself to you. Once you’re in, there are also runtime health checks: blockchains and DHTs are combined with off-chain pings, gossip, or indexers to confirm which peers are currently reachable.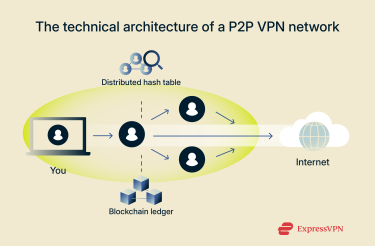
To encourage people to share their bandwidth, some of these platforms also have built-in economic models and incentives. Users who contribute their connections to the network may receive some form of benefit, either financially or through an extension of their subscription.
This incentive system helps ensure there are enough nodes to keep the network running and provides a reward for supporting the community.
How P2P VPN differs from commercial VPNs
Here’s how a P2P VPN stacks up against a commercial VPN. Note that the quality of P2P VPNs can vary a lot and can also be hard to assess.
| Feature | P2P VPN | Commercial VPN |
| Architecture | Network of user-operated nodes. You can opt to run a node; by default, you’re a client. | Network of company-operated servers managed by a provider. |
| Trust model | Trust is distributed across protocol implementation and independent node operators. | Trust is placed in the VPN company, its policies, and its audits. |
| Performance | Often variable and dependent on other users’ nodes and links. | More predictable and usually faster, using provider-operated high-speed servers. |
| Accountability | No single operator runs all nodes. Support tends to be project or community-led rather than from the exit you use. | The company is fully accountable for security and performance. |
| Logging | In general, no central provider holds all activity data. Some P2P VPNs offer multi-hop design to make it difficult to trace your online activity back to you, but a single exit node can observe plaintext on non-HTTPS sites. | Depends on the provider’s policy. Look for an audited no-logs policy. |
| IP address | Your IP is hidden behind another user’s exit IP. You don’t act as an exit unless you install and run node software. | Your IP is hidden behind provider-operated IPs, typically shared among many users, with optional dedicated IPs from providers like ExpressVPN. |
| Customer support | Generally limited to community forums or possibly email tickets. | Typically extensive support options: email, live chat, detailed tutorials, etc. |
| Complexity | Generally challenging to set up, configure, and manage, requiring more technical knowledge and effort. | Typically easy to set up and use, with intuitive apps for all the major operating systems. |
Perhaps the most important difference of all listed above is that the P2P VPN model doesn’t eliminate the need for trust, it redistributes it. Instead of relying solely on a central provider, you also have to trust the network’s node operators, who could be anyone. This adds complexity and poses additional security risks unless you build your own P2P network with explicitly trusted peers, which isn’t realistic for most users.
While spreading traffic across numerous nodes makes it difficult to trace online activity back to a single user, it’s vital to know that the first node always sees your IP. What’s more, it might see your traffic as well if the VPN technology isn’t well-designed; misconfiguration or weak clients can degrade privacy, even with layered encryption. This means you’re putting your trust in the provider’s infrastructure (which can be hard to verify), and the first node your traffic passes through.
When you’re part of a P2P VPN network and decide to become an exit node, you’re letting anyone use your router for whatever they need, and this presents obvious legal risks. If someone uses your exit IP address for any kind of prohibited activity, you could receive a notice from your internet service provider (ISP) or even face legal action. What’s more, the decentralized nature of P2P VPNs means internet traffic often routes through multiple countries with varying legal frameworks, adding another layer of legal complexity.
Apart from privacy and legal risks, there are also security concerns: it only takes one malicious node to monitor unencrypted data, attempt to inject malware, or analyze your traffic patterns, posing a direct security threat.
In contrast, when you choose a commercial VPN provider, you’re trusting the company with your data. Just as with a P2P VPN, it’s important to choose carefully, as not all commercial VPNs are created equal, and there are some products that might sell or log your data. However, unlike with P2P VPNs, it’s fairly easy to verify this information.
For example, ExpressVPN has passed multiple third-party audits confirming the validity of its no-logs policy, privacy policy, protocols, apps, and server technology.
What is a P2P VPN used for?
P2P VPNs are a niche technology, but they can serve a few specific purposes:
- Research and experimentation: Some developers and researchers have used decentralized networks to explore how internet connections can remain resilient without relying on central servers.
- Community bandwidth marketplaces: Certain projects, such as Mysterium and Orchid, allow participants to share or trade unused bandwidth, supporting the network’s capacity and reach.
- Extending network reach: In places where traditional VPNs have limited server coverage, peers in those areas may act as temporary “exit points,” though this depends entirely on who is connected and comes with privacy and reliability trade-offs.
How to assess a P2P VPN
If you’re considering using a P2P VPN, here’s what you need to check before committing.
Information on the developers and code
While the network is decentralized, the technology behind it was created by developers. It’s a good idea to research who it was developed by, the reputation of the organization behind it, and whether the code is open-source and is actively maintained and reviewed. You can also check for third party audits, but these are fairly rare with decentralized VPNs.
Strength of encryption
A VPN is only as secure as the encryption that protects your traffic. Some P2P VPNs use proven protocols like WireGuard and OpenVPN, while others rely on custom or experimental cryptography. Always check the technical documentation, GitHub repository, or whitepaper for details on the encryption protocols used, and look for 256-bit Advanced Encryption Standard (AES), ChaCha20 or equivalent proven and secure ciphers. You should also check whether the encryption protects against quantum threats through the use of hybrid Rivest–Shamir–Adleman (RSA) and Module Lattice-Based Key Encapsulation Mechanism (ML-KEM) keys. If you can’t find this information you should exercise caution, as transparency about cryptographic design is standard for established products.
Reliability and verification of nodes
One of the major risks of a P2P VPN is that your traffic passes through strangers’ devices. For this reason, it’s really important to check how the nodes are verified and incentivized and what protections are in place to prevent malicious peers from intercepting your traffic. Review the VPN’s technical documentation to find details on these aspects.
Multi-hop or onion routing options
One of the strongest privacy protections a P2P VPN can offer is multi-hop or onion routing (where traffic is encrypted and passed through two or more servers before reaching its destination). When assessing a provider, look for explicit mentions of multi-hop or onion routing in the technical documentation. Also, check for details on whether information is encrypted across all hops, and if possible, check the project’s GitHub or white paper for details on how paths are built and verified.
Note, however, that even if a P2P VPN provider advertises multi-hop, there’s no guarantee every hop is configured securely.
Customer support
Unlike commercial VPNs, P2P VPNs rarely offer comprehensive customer support. If being able to access support for aspects like device setup and troubleshooting is important to you, you should look carefully at how the P2P VPN defines “support.” For example, does it offer live chat and email tickets, or just community forums? Also, is support restricted to paid users? Check the site for documentation, FAQs, and community resources, too. Good self-help materials matter, especially if direct support is minimal.
Size of network
The quality of a P2P VPN depends on how many participants are online and how evenly they’re spread across geographic regions. A large, geographically diverse network will generally offer more routing options and less congestion. However, node counts can fluctuate dramatically, especially if participation relies on token rewards or volunteer activity. To assess this, check whether the project publishes live network statistics. You can also explore community forums to check how active the network really is.
User reviews and ratings
Real-world feedback from users can help to reveal recurring issues like instability or node reliability. Check independent sources like Reddit, Trustpilot, or app store listings, and look for consistency across multiple platforms. Also note the frequency and responsiveness of developer replies, because active engagement is more likely to signal a legitimate project.
Overall, if you want reliable encryption, clear accountability, and consistent performance, a reputable commercial VPN like ExpressVPN is the more practical choice for most users.
FAQ: Common questions about P2P VPNs
How does a P2P VPN enhance privacy?
A peer-to-peer virtual private network (P2P VPN) replaces your personal IP address with one from its shared network and encrypts all your internet traffic. However, because the network is operated by users rather than a central company, a malicious node could potentially monitor unencrypted data, putting your privacy at risk instead of protecting it.
What should I consider when choosing a P2P VPN provider?
There are several key considerations, including peer discovery method, single-hop vs. multi-hop, how exits are vetted, reputation, and the project’s stance on logs. If you want to run an exit node, make sure you understand the legal implications.
Are P2P VPNs safe for sharing files?
Using a peer-to-peer virtual private network (P2P VPN) may make file sharing safer by encrypting your traffic and hiding your IP address, but it only takes one malicious node to start exposing files. Also, remember that files downloaded from P2P networks can contain malware. What’s more, you should only download or share content you have a legal right to access; laws vary significantly by location, and if your connection is used as an exit point by others, their illegal activities could be traced back to your IP address.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN