What is biometrics? A complete guide to modern identity technology

Each person has distinct biological traits, from fingerprints and facial features to vocal patterns and more. These bits of biological data, known as biometrics, have an increasing number of uses in the modern world, especially in cybersecurity, where they help secure accounts, data, and devices.
This guide explores what biometrics are, how they’re used, the benefits they bring, and also the challenges they pose.
What is biometric data?
Biometric data simply refers to data that focuses on people’s physical or behavioral characteristics or attributes. This includes fingerprints, facial features, retinal scans, and so on. This data can be used to identify and recognize individuals. For example, a user might be able to unlock their phone by putting their finger on the phone’s fingerprint scanner.
How biometric data is collected
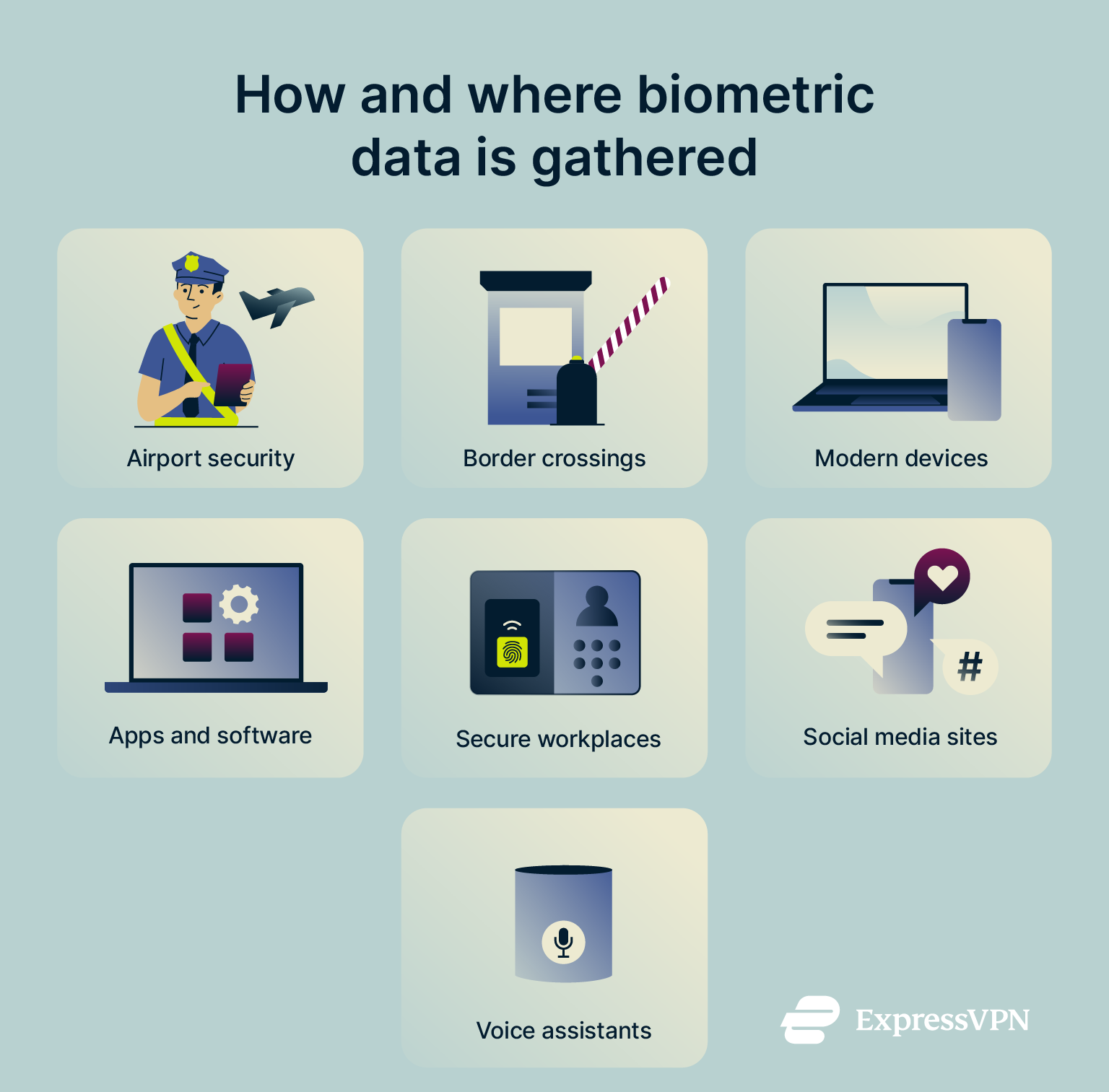
Biometric data is collected in numerous ways and by various organizations, from governmental agencies to tech giants and social media companies. Here are some of the many ways in which it can be gathered:
- When setting up new devices, like phones or computers, which have some sort of biometric authentication technology built-in, like face or fingerprint scanning.
- At airports and border control services, where authorities may take pictures and fingerprint scans of travelers passing through.
- When using DNA analysis services, such as those designed to help people learn about their family’s ancestry.
- When using certain apps that are able to collect, create, and store biometric data, like facial photographs or voice recordings of their users.
- At workplaces that use biometric authentication or identification technology, like those with retina- or fingerprint-controlled doors or access panels.
- When interacting with AI voice assistants, such as Alexa or Google Home, which can collect user voice data.
- On certain social media platforms, like TikTok, which updated its policies in 2021 to allow for the collection of user biometric data.
Where biometric data is stored
Given its sensitivity, biometric data has to be stored securely. There are various ways of doing this:
- On-device storage: This involves storing the biometric data locally, on the device it was collected on and will be used on. If you set up facial recognition on your phone, for example, the data is typically stored only on that phone.
- Biometric servers: Sometimes, biometric data is stored on secure biometric servers, which may be physical or cloud-based.
- Distributed storage systems: This method effectively involves a mixture of the other two, with certain parts of biometric data remaining on the device and others being stored on secure servers, offering a blend of security and accessibility.
It’s worth noting that biometric data is often encrypted and stored as a template rather than as a raw image. This improves security; if the data is leaked or accessed by an unauthorized user, it’s much harder to decrypt or misuse.
Types of biometric identification
Biometric data comes in numerous forms, including the most obvious and well-known examples, like fingerprints, and lesser-known alternatives related to behavior or less prominent physical characteristics. We can divide these varieties into two distinct groups: physical and behavioral.
Physical biometrics
Examples of physical biometrics include:
- Fingerprints
- Finger geometry (shape and size of fingers)
- Eye scans, including retina and iris
- Facial features
- Ear shapes
- Heartbeat patterns

Behavioral biometrics
Behavioral biometrics include:
- Vocal and speech patterns
- Signature
- Typing patterns
- Gait (how a person walks or runs)
How biometric authentication works
Biometric authentication works by first capturing and converting a user’s biometric data into a digital template, which is typically encrypted for security. When the user later attempts to authenticate, the system captures new biometric data and compares it to the stored template. If there's a match, access is granted.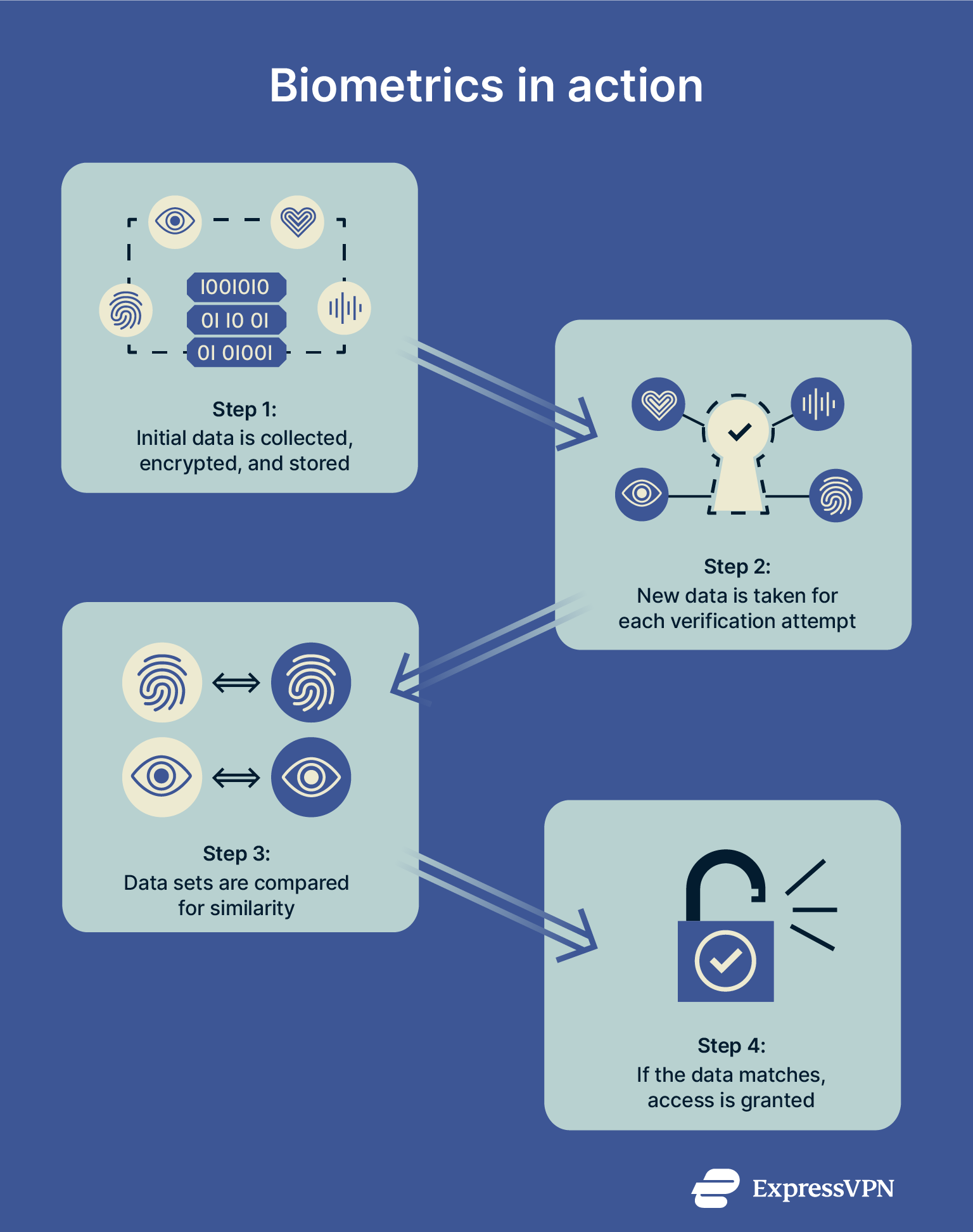 Let’s now illustrate this with an example:
Let’s now illustrate this with an example:
- A user buys a new smartphone with a fingerprint sensor built in.
- When setting up the device, they are asked to scan their fingerprint, which they do by placing their finger over the sensor at various angles while the system collates the data.
- The biometric fingerprint data is then encrypted and secured on the device.
- The next time the user wants to unlock their phone with their fingerprint, they place their finger on the sensor.
- The device collects fingerprint data again at this moment and cross-references it with the secure biometric data gathered earlier on. If the two match, the device unlocks.
Benefits of using biometrics
The main benefits of using biometric technology include:
- Enhanced security: For a long time, passwords were the main way of securing accounts, but they can be guessed or hacked. Biometrics are unique to every individual and much harder to fabricate, making accounts, devices, and data more secure.
- User convenience: It’s much simpler for users to just tap their finger on a device or do a quick face scan to unlock something or access an account than to memorize and type in strong passwords each time; at least, that’s the case if you don’t use a secure and intuitive password manager.
- Versatile applications: There are many ways in which we can use and apply biometric data. It’s already in use across a vast range of industries, from finance and banking to healthcare, education, technology, and beyond.
Risks and challenges of biometrics
Despite their many benefits, biometrics aren’t perfect. They bring certain challenges and risks to the table, which must be acknowledged and countered, where possible.
Can biometrics be hacked?
It might seem impossible for biometrics to be hacked, since they’re entirely unique pieces of data, specific to every individual. Unfortunately, they can be hacked, especially with the aid of modern technologies like AI.
In 2018, researchers from New York University Tandon and Michigan State University created fake fingerprint images that can fool fingerprint scanners into thinking they’re real, and not just real, but real enough to unlock many different people’s devices. They used generative adversarial networks, computer programs that learn to create images that look like the real thing (in this case, fingerprints), to generate tons of fake fingerprints, tested how well each one could fool a fingerprint system, and kept tweaking them until they found the best “super fingerprints.” The result is what they called DeepMasterPrints, fake fingerprints that can unlock phones or devices without knowing the actual user’s fingerprint.
Instead of imitating biometric data, cybercriminals can also steal it through skimming, which involves using special devices to capture fingerprint data from machines such as ATMs. Biometric data can also be exposed through leaks or database breaches. If cybercriminals gain access to this data, they may be able to decrypt it and use it for malicious purposes.
Privacy and identity concerns
Many people have also raised concerns about the risk that biometric data collection poses to people’s privacy. Those who care about their privacy or have concerns about how their data may be collected, stored, and used by various companies or agencies may be fearful about such organizations having their fingerprints, eye scans, and facial photos on record.
Whenever any kind of personal data is gathered and stored, there are always going to be concerns about how it might be used or what would happen if it fell into the wrong hands. Even with powerful encryption and other security measures, like on-device storage, there are still risks of cybercriminals acquiring this deeply personal data, putting privacy at serious risk.
Are biometrics safer than passwords?
Generally speaking, yes, biometrics are largely considered safer than passwords. This is because, as stated, biometric data is unique. Everyone has their own specific fingerprints, facial features, etc. This rules out poor cybersecurity habits as a risk factor. Passwords, meanwhile, can easily be cracked if they’re not strong enough and copied.
Because of this, accounts or devices secured by biometrics are typically harder for cybercriminals to get into than those simply protected by passwords. However, this is not to say that biometric protections are problem-free. As discussed, there are ways to fool biometric verification systems or steal biometric data.
How to protect your biometric data
You can counteract the risks of biometric data by following certain best practices and taking a cautious, measured approach to digital security.
Best practices for individuals
- Think before you opt in: Don’t just click the “Accept” button without thinking if and when companies ask for your biometric data. Think about the risks involved and consider opting out if you’re not completely confident.
- Use several levels of protection: It’s best to not only rely on passwords or biometrics to guard your accounts. Instead, use multiple layers of protection, including two-factor authentication (2FA) and multi-factor authentication (MFA), to make your identity much harder to imitate or steal.
- Connect to a VPN: By connecting to a VPN, your internet traffic, which includes any biometric data you send or receive, will be encrypted and therefore much harder for anyone to intercept. This is particularly important on public or insecure Wi-Fi networks.
How companies should secure biometrics
Companies handling biometric data need to take all necessary steps to encrypt and protect it, reducing the risk of data loss, breaches, leaks, or theft. This may include:
- Designating clear security leaders, responsible for biometric security management.
- Implementing secure data storage policies.
- Training employees on how to manage and secure biometric data.
- Setting clear access controls about who can access the data and how.
- Carrying out risk assessments and audits to identify possible weaknesses.
- Consulting with cybersecurity professionals for expert insight and advice.
The future of biometrics
Biometrics aren’t going away. Predictions suggest that the industry will nearly quadruple in value between 2025 and 2033, and biometrics are becoming more and more commonplace on devices, software, and working environments. We can expect to see biometric authentication included with future computers, smartphones, wearables, and smart home devices. And multimodal biometric systems, which use multiple pieces of biometric data, like fingerprints and voice scans, for enhanced security and stricter access control, are expected to become more widespread.
FAQ: Common questions about biometrics
What is biometrics in simple terms?
In simple terms, biometric data is data that refers to a person’s physical or biological characteristics, like their fingerprints or voice patterns.
What is an example of using biometrics?
An example of biometrics in action would be using your fingerprint to unlock your phone or doing a face scan to access an online account.
What is the purpose of using biometrics?
Biometric authentication is designed to be a more secure and convenient alternative to conventional passwords.
What is biometric verification?
Biometric verification is the process of using biometric data, like fingerprints, to protect an account and verify a user’s identity.
Is biometric data stored on my device or the cloud?
It depends. Some companies store it on the device only, while others store it in the cloud or on physical servers.
Can I delete my biometric information?
It depends on where you live, and laws are rapidly being developed and modified in relation to biometric data. In some countries, you can request that your biometric data be deleted from company records, but there’s no guarantee that all traces of it will be completely removed. You can also delete registered biometric data, like fingerprints, from certain devices, like phones.
What happens if biometric data is stolen?
Stolen biometric data may be used to imitate a user and gain access to their private data or accounts. It could be used for fraud, identity theft, and other forms of cybercrime.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN